Blog
How To Defend Against Cyber Security Threats?
Cyber Security threats have grown more complex in the current digital era, putting people, companies, and governments at serious risk. Being proactive in Read More...
The Benefits of Cybersecurity Education for Business?
It is impossible to overestimate the significance of cybersecurity for businesses in the increasingly digital world of today. Cyber threats are constantly changing Read More...
The Benefits of AWS Certification
Stepping into the tech terrain, you've probably caught wind of the continually buzzing phrase - AWS certification. Standing as a lynchpin of the cloud computing sphere Read More...
Is Ethical Hacking Legal and How Does It Differ from Cyber Crime?
It is known as white hat hacking, which uses hacking techniques to identify and exploit vulnerabilities in computer systems & networks with the Read More...
Women in Ethical Hacking: Breaking Barriers and Shaping the Future
It is a growing field essential for protecting organizations from cyber-attacks. While it is a rewarding career, it is also male-dominated. Read More...
10 Essential Skills Every Web Developer Should Master in 2023
The Web Development landscape is constantly changing. Technologies and trends are emerging all the time on the internet. Read More...
Unleashing the Power of Python: Benefits of Studying Python Programming IIEHT
In today's digital age, computer programming has emerged as an essential skill across various industries. One programming language that has Read More...
Understanding Cyber security: Ensuring a Secure Digital Future
In today's interconnected digital age, the importance of cyber security cannot be overstated. The Indian Institute of Ethical Hacking & Technology (IIEHT) Read More...
Exploring the 5 Different Phases of Ethical Hacking
With the tremendous dependence on technology, the risk of cyber threats has grown exponentially. To combat this, ethical hacking has emerged as a crucial tool in addressing vulnerabilities and Read More...
Best Programming Languages
A number of jobs and projects, such as online applications and video games, can be carried out by IT professionals using programming languages.Read More...
What is a Certified Ethical Hacker?
An expert who is trained to look into a system's flaws and vulnerabilities and attempt to protect it from harmful attacks is known as a Certified Ethical Hacker. Read More...
Top 10 high paying jobs
We all learn at a young age that a good career ensures a nice life. Students can brush up on their abilities and land some Read More...
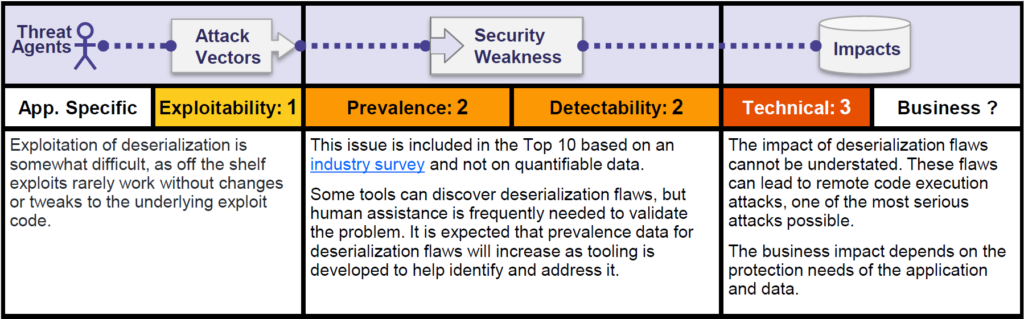
Insecure Deserialization
The process of serialization involves flattening complex data structures, like objects and their fields, so they may be Read More...
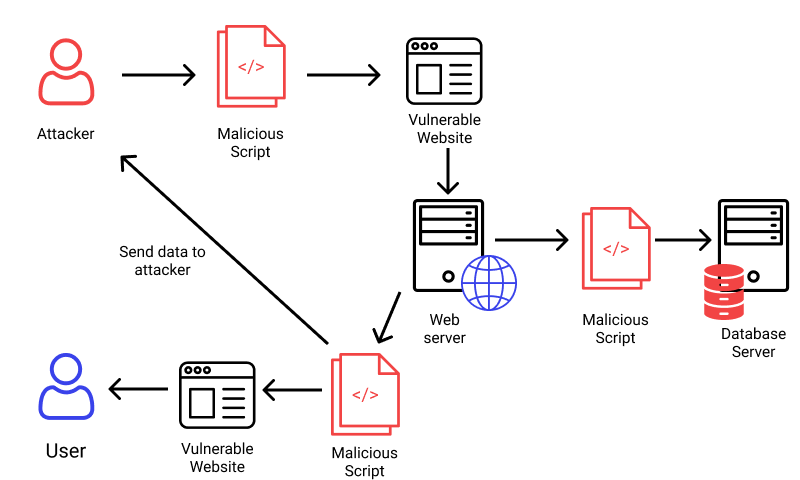
Cross site scripting
The intricacy and complexity of XSS make it one of my favourite vulnerability types. When you truly look at XSS, there is a world of Read More...
Broken Access Control
Due to the design and implementation of access control systems relying on a very complex ecosystem of many components and processes Read More...
Social engineering attack: what is it? What techniques and prevention methods exist