Owasp top 10
Date: March 03, 2023
Owasp
Introduction
In the most recent period, businesses have been using the internet to carry out routine duties, including handling sensitive data and intricate workflows, in addition to using it to promote their brands, goods, and services. Furthermore, many applications are switching from their traditional desktop-based versions to web-based ones in order to target a wider range of portable devices with cheap cost and portability to the acceptance and proliferation of advanced handheld electronics. As a result, enterprises have significant security issues in securing their web applications. On the other side, the number of attackers is continuously expanding, and their attack strategies are becoming more dangerous and complex (WAs). As a result, the security of WHAs become a crucial study subject, and many solutions have been put forth to safeguard the WA. From a different angle, security administrators frequently install WAFs (WA Firewalls) to defend the WAs. The WAFs frequently employ rudimentary protection measures as opposed to the cutting-edge methods advocated by the researchers, as will be demonstrated later in this work. Modern web protection techniques differ significantly from those used by the WAFs now in use. By defining the most severe online attacks and the suitable defences against each attack, this research aims to close this gap. The most widely known web vulnerabilities, which were published by the OWASP group, are used to identify the critical assaults.
A group of international security specialists from several countries put together the report. OWASP refers to the Top 10 as a "awareness document" and suggests that all companies include the report into their practices in order to lessen and/or mitigate security concerns.
The security concerns included in the OWASP Top 10 2017 report are as follows:
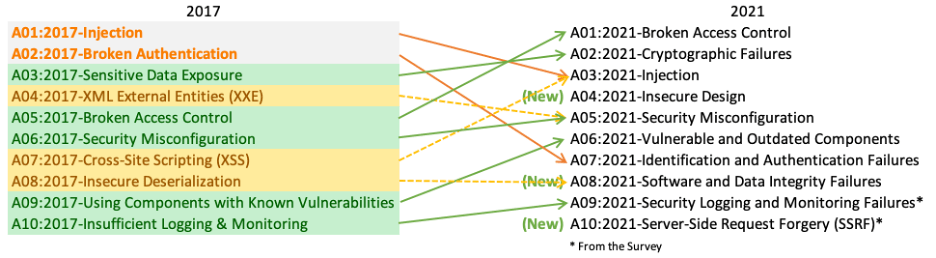
1. Injection : Injection attacks happen when untrusted data is provided to a code interpreter through a form input or similar data submission to a web site. For instance, a hacker could utilize SQL database code to fill out a form that asked for a plaintext username. Incorrect form input protection would cause the SQL code to be executed. What this is a SQL injection attack. User-submitted data can be made more accurate and/or clean to help prevent injection attacks. Validation refers to accepting data that appears valid whereas sanitization refers to removing suspicious-looking elements of the data.
The following are the injection attacks that are most dangerous:
• SQL Injection : In order to get access to a database (DB) or alter its contents, such as by deleting or modifying database content, SQL commands are injected into input forms or queries.
• Code injection : Code injection is an attack that takes advantage of sloppy handling of untrusted data by injecting code that the application interprets and executes.
2. Broken access Control : Broken Access Control has risen to the top spot as the category with the biggest web application security risk; the data provided reveals that, on average, compared to other app categories, Broken Access Control has the most instances of the 34 CWEs. Attackers may be able to access user accounts via security flaws in authentication (login) systems, and by using an admin account, they may even be able to take control of the entire system.
The following categories have been ascribed to this attack:
• Brute force attack : This technique involves guessing a user's password by trying various character combinations.
• Dictionary Attack : The attacker might plan a dictionary attack if he knows something about the target (set of valid words). The victim's password is then deduced by combining these terms.
• Attack on Credentials : In this type of attack, the attacker tries to gather legitimate usernames for a password-guessing campaign by employing verbose error messages that indicate whether the login is a legitimate username or not.
3. Sensitive data Exposure : Web applications must protect sensitive data, including passwords and financial information, to prevent access by hackers who might sell or use it for illegal purposes. An effective method for stealing sensitive information is an on-path assault. The danger of data disclosure can be decreased by encrypting any sensitive data and preventing caching of any sensitive data. Web application developers must also take care not to keep sensitive data around unnecessarily. Caching is the process of temporarily storing data for use at a later time. In order to avoid having to fetch webpages from the internet each time a user returns to them after a set amount of time, web browsers routinely cache webpages.
• Transmission Attack : When connection between the client and the web server is not encrypted, all data exchanged between the two is sent in clear text, making it vulnerable to interception, injection, and redirection.
• Database Theft : An attacker could steal sensitive data from a database if adequate encryption or access controls aren't in place to secure it. Attacks on three databases are possible: SQL injection, a brute-force attack, and privilege escalation.
4. XML External Entities : This is an assault on a web application that reads input from XML files. In an effort to weaken the parser, this input might make reference to an external source. An "external entity" in this sense refers to a storage device, such as a hard disc. It is possible for an XML parser to be tricked into transmitting information to an unauthorized external entity, which could then pass private information to an attacker. The strongest protection against XEE attacks is having online applications accept a fewer complex data format, like JSON, or, at the very least, patching XML parsers and disabling the use of external entities in an XML application.
5. Inefficient Access Control : An access control system is one that limits users' access to data or features. Attackers have the capacity to get around restrictions and behave as administrators or other privileged users when access controls aren't functioning properly. For instance, an online application might let a user switch between accounts by merely altering a portion of the URL, with no extra authentication required. By making sure at a web application uses authorization tokens and places strict controls on them, access controls can be made safe. When users log in, many services give authorization tokens.
6. Security Misconfiguration : The most frequent vulnerability on the list is security misconfiguration, which is frequently caused by default configurations or overly verbose error messages. For instance, a user may see excessively descriptive errors in an application, which may indicate the application has flaws.
7. Insecure Deserialization : The numerous web apps that constantly serialize and deserialize data are the target of this danger. Serialization is the process of extracting objects from application code and transforming them into a format that may be utilized for other operations, such as streaming data or saving it on disc. Deserialization is the exact reverse, turning serialized data into usable objects for the application. Deserialization is similar to unpacking the boxes and reassembling the furniture after a move, whereas serialization is similar to packing the furniture away into boxes before one.
8. Using components with known vulnerabilities : In their web projects, many contemporary web developers use components like libraries and frameworks. These components, which are pieces of software that save developers time and provide the functionality they need, are frequently used in front-end frameworks like React and smaller libraries to add share icons or do a/b testing. Some attackers examine these components for flaws they can take advantage of while devising attacks. A vulnerability in one of the more popular components, which is used by hundreds of millions of websites, might leave such sites vulnerable to attack. Although component developers routinely release security updates and fixes to close known vulnerabilities, web application developers don't always have the patched or most recent versions of components running on their apps. To lessen the possibility of running components with known vulnerabilities, developers should remove unneeded components from their projects, ensure they are receiving components from a trusted source, and ensure they are up to date.
9. Inadequate monitoring and logging : Many web apps don't take the necessary precautions to spot data breaches. Usually, a breach is found 200 days after it took place. Because of this, attackers have plenty of time to cause harm before a defence can be deployed. The OWASP organization urges web developers to create logging, monitoring, and incident response systems to make sure they are aware of attacks on their applications.
10. Cross site Scripting : Cross-site scripting vulnerabilities appear when web applications allow users to enter custom code into a URL route or onto a website that is visible to other users. A victim might receive an email from what appears to be a credible bank that links to the bank's website, for example. This link may have malicious JavaScript code at the end of it. If the bank's website is not sufficiently protected against cross-site scripting, when the victim clicks on the link, their web browser will run the malicious code.