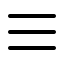Injection
Date: March 07, 2023

Injection
Introduction
Injection is a sort of cyberattack that sends data to alter how commands are processed by the system. An attacker will send malicious data to an interpreter during an injection. The majority of data sources, such as environment variables, parameters, web services, and user types, can be utilised for data injection. Application risks like injection, which are among the Top 10 OWASP risks, should be watched out for. The 10 most risky web application security flaws are listed in the OWASP Top 10 report. To ensure that the top ten most serious dangers to businesses are always included on the list, it is regularly updated. OWASP recommends that all businesses incorporate the document's recommendations into their internal business procedures in order to ensure that they lessen and mitigate the biggest security risks. To make their web apps less static, developers frequently use certain strategies. This can involve things like database CRUD operations, LDAP login operations, or OS commands. These are only a few examples of how a developer can make a web application less static, and they all have the same potential security flaws that appear when user data is processed without being sanitised. At this point, people with malicious intent have the opportunity to introduce their own malicious input into these processes, which can have severely negative results, such as SQL injection. You do not want to miss out on this top 10 OWASP issue type.
What are the dangers of getting injected?
Injection may result in data loss, corruption, and breaches, as well as loss of control and the disclosure of private data pertaining to the target host. Attackers may gain unauthorized access to the database as a result of a "successful" injection, enabling them to view tables, read important data from them, update them, and even gain administrator access. In 2007, a SQL injection allowed hackers to access 7-Eleven servers. Credit card numbers were accessible, and they were able to send money to themselves. RTF Template Injection, a new kind of injection assault recently linked to state-sponsored threat actors from China, India, and Russia, has come to light.
Types of Injection
SQL injection (SQLi) and cross-site scripting (XSS) are the two most common types of injection attacks; however, they are not the only ones. There are various injection attacks, including:
• SQL Injection: An online security hole called SQL injection gives an attacker the possibility to alter the SQL queries that are sent to the database. Sensitive data such database structure, tables, and columns, as well as their data set, may be extracted using this. The CWE Top 25 list of vulnerabilities consistently includes SQL injections, one of the most severe online application flaws: Incorrect SQL Command Neutralization of Special Elements (CWE-89).
• LDAP Injection: Directory services on IP servers are accessed and managed via LDAP (Lightweight Active Directory Protocol). In addition to providing access to a directory database, LDAP is a client-server protocol used for resource management, authentication, and permission control. Malicious LDAP queries are sent to the server when an attacker inserts dangerous statements; this has an impact on server security. The attacker will have access to confidential information and be able to change the LDAP structure if they are successful in the LDAP injection.
• XML Injection: As developers, we occasionally might need to provide XML input. This XML file can take on a variety of formats; upload functionality is not just restricted to pure XML files. This problem can appear in a variety of forms, from SOAP calls that include user-supplied input to XML files that will also use that input to construct the file. The attacker will try to input values that will mess with the produced XML file's structure and try to insert their own values.
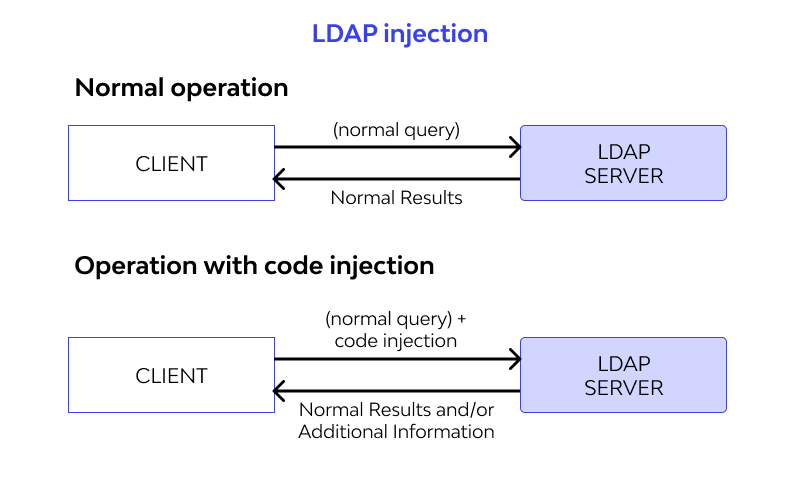
• OS Command Injection: A vulnerability called OS Command Injection, commonly referred to as shell injection, enables an attacker to run whatever commands they choose on the server of an active application. The operating system, acting as the web server, executes the inserted arbitrary commands. Although these command injection issues may not by themselves cause a full system compromise, attackers can utilize privilege escalation and other vulnerabilities to exploit them.
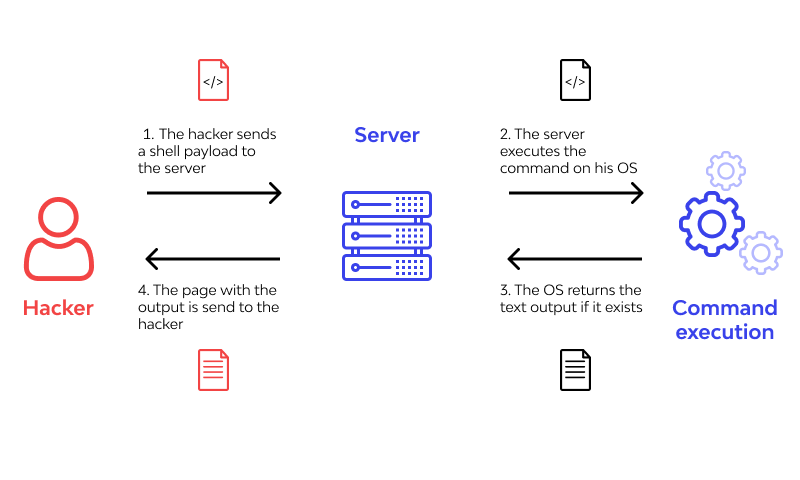
• CRLF Injection: Carriage Return Linefeed, or CRLF, is a unique set of characters that the HTTP protocol uses to demarcate lines. The programme reacts to a CRLF injection by returning a header response that contains the attacker's CRLF sequence and any adjacent data the hacker has provided. Web page hijacking and other pertinent tactics are used in this attack.
• Host Header Injection: The host header of a website or web application specifies which website or web application will respond to an incoming HTTP request. In order to transmit the request to the specified website or online application, the web server uses the value of this header. The attacker could poison the web cache and carry out illegal activities like password reset if they send an arbitrary host to the real virtual host.
• Mail Command Injection: Mail Command Injection is a form of attack that targets mail servers and webmail programmes that produce IMAP/SMTP statements from unfiltered user-supplied data.
If the attacker knows the port number on which the mail server is running, he will be able to directly contact it. A contact form that is vulnerable might be used to distribute spam or launch phishing attacks, even if email injection does not directly endanger the owner of the web server.
How Are Injections Preventable?
The following techniques can be used to look for injection vulnerabilities in your systems:
1. The simplest method is to highlight a parameter in the address bar of your browser, followed by a single quote ('). For instance, replace "username=" with "username=" and emphasize the value. As in "username=name," the single quote may also be put inside the argument's value. If you notice a field that has been omitted or a response that includes data, you could be in danger.
2. Use the free tool SQLMAP from Kali Linux. Using SQLMAP, SQL Injection may be located and researched.
3. To cxheck for cross-site scripting, copy your test script and paste it into the database's input field. You will notice exposed data in the JavaScript response if there is a vulnerability.
4. If your source code employs specific techniques like XML or JSON parsers, which permit making requests, your software may be vulnerable. Various issues, including those in the "'" or bash commands, should be fixed.
Here are some recommendations for avoiding OWASP injection vulnerabilities:
• Authenticate Users: Servers and software that are available to everyone online are frequently the targets of injection attacks. Sharing responsibility for stopping these threats with server administrators and application developers. Regular system audits and secure user authorization techniques like MFA are essential for preventing injection.
• Prevent File Uploading: Malicious malware can be found in files. Therefore, it should not be possible to submit files that include banned extensions or macros. Verify file extensions and only permit common file extensions, like PDF, CSV, or txt, to be uploaded by normal users.
• Validate Data: Input validation makes ensuring that only properly formatted input enters an information system's process, avoiding inaccurate and harmful data from staying in the database. Developers validate data by comparing the value of the data to the stated set of rules and analyse data within necessary constraints.
• Review Configurations: Examine the technologies your application use and the information accessible on their misuse. Technologies that are out of date could be attacked. JavaScript and jQuery plugins are two examples of these dangerous technology.
OWASP Top 10 Attacks and Other Prevention using Zero Trust
Zero Trust is a security architecture that restricts an organization's network, application, and environment without impairing performance or user experience. It is built on a stringent identity verification process. Only authenticated and authorized users and devices are able to access applications and data using the zero-trust architecture. In order to prevent any unauthorized users or access to restricted resources, any attack, including a code injection, will be recognized as being beyond the expected range of behaviours and This will result in either a warning or the closing of the application session. When the zero-trust framework is used, attackers won't be able to see potential OWASP applicable vulnerabilities.